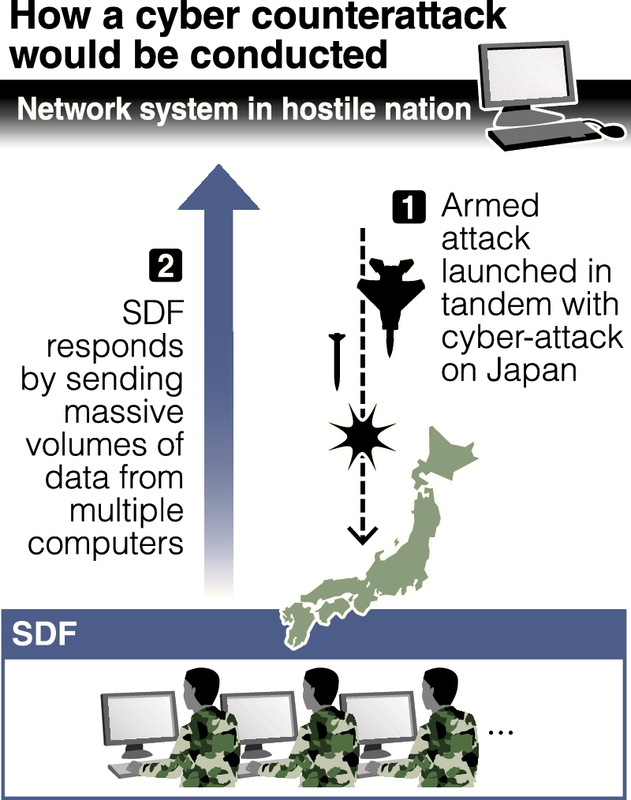
The government is arranging for the Self-Defense Forces to possess the equipment and ability to counter cyber-attacks launched against the nation, The Yomiuri Shimbun has learned.
Any such counterattack would be conducted only if the nation also came under a physical attack involving conventional weapons and other threats. The most likely counterpunch would come as a distributed denial of service (DDoS) attack, in which massive amounts of data would be sent to servers in bases the hostile nation used for the attack. A DDoS attack would paralyze these servers.
The government is considering spelling out these operations in the National Defense Program Guidelines, the basic plans for Japan's defense policies, which will be compiled by the end of 2018.
The Medium Term Defense Program for fiscal 2014 to fiscal 2018 stipulated, "In cyberspace, where attackers have an overwhelming advantage, the SDF may consider the acquisition of capabilities to prevent them from using cyberspace." Since then, the government has been chewing over the arguments for and against possessing these capabilities. Consequently, the government decided that having the capability to counter a cyber-attack recognized as being conducted in line with the "organized and planned use of force based on a state's will against Japan" would not contradict the nation's exclusively defense-oriented security policy.
In many cases, a cyber-attack is conducted after taking over the server of a totally unrelated third party. Accordingly, determining that a cyber-attack by itself "was the exercise of force based on a state's will would be difficult," a senior Defense Ministry official said. Because of this, the SDF would be permitted to launch cyber counterattacks only when Japan had been targeted by a cyber-attack accompanied by an attack with conventional weapons. The government assumes such cases would involve a cyber-attack launched integrally with a ballistic missile attack or an invasion in which enemy forces come ashore on Japanese territory.
The SDF's current approach centers on a cyber defense unit that is acquiring the skills and knowledge needed to conduct a cyber counterattack. According to a senior Defense Ministry official, "If a substantial number of computers and other equipment dedicated to conducting a counterattack were put in place, it would be possible to quickly send a flood of data to an adversary's servers" as a DDoS attack. The SDF also is preparing to test the vulnerability of its internal systems by checking their ability to withstand a cyber-attack.
However, the most common form of cyber-attack used internationally involves malware (see below) that enables a third-party's server to be used to send huge volumes of data. These attacks do not require preparing large amounts of hardware. But Japan's criminal law prohibits creating or possessing malware without a legitimate reason, so the SDF's possession of such programs for the purpose of a counterattack remains an issue that will require serious discussion from now on.
In line with its review of the defense guidelines, the government plans to strengthen countermeasures that boost its ability to defend cyberspace in addition to giving the SDF the capability to launch cyber counterattacks. Among steps being considered are increasing the number of personnel assigned to these duties, working closely with private companies and using artificial intelligence.
-- Malware
Malware is a contraction of "malicious software." Viruses and worms are among the main types of malware, which are designed to operate a computer without any intention on the part of the owner, who unwittingly receives them. Malware is often used in espionage activities to steal confidential information and other data.
Read more from The Japan News at https://japannews.yomiuri.co.jp/







