
CHENNAI: Last year, Kirthika* continuously received sleazy messages and nude photographs on her mobile phone from a stalker for nearly two months.
The 16-year-old Chennai resident lodged a police complaint. The stalker deleted the messages and broke his mobile phone, believing he could go scot-free. But, using a highend data extraction tool procured by the Tamil Nadu Forensic Department, police managed to retrieve all the messages and media files. The stalker is now in jail.
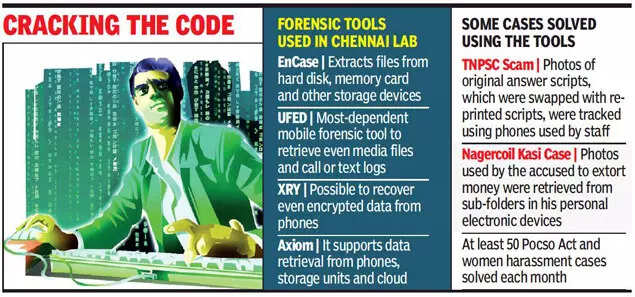
Retrieving such deleted files from damaged electronic devices is possible due to Universal Forensic Extraction Device (UFED), a mobile tool available at Chennai Forensic House, Mylapore. The lab has other globally-accepted software tools such as EnCase, XRY and Magnet Axiom, which extract crucial evidence from not only mobile phones (Android and iOS) but also from storage devices (laptops, hard disks, pen drives and memory cards) and CCTV cameras.
Ever since the Covid-triggered lockdown, there has been a three-fold rise in the Prevention of Children from Sexual Offences (Pocso) Act and women harassment cases dealt by Chennai Forensic House. On an average, every month, the lab deals with at least 50 such cases a month. Earlier, it was less than 15, according to police data. In almost all these cases, the lab reports have helped police get the perpetrators convicted by courts.
“Though there are hundreds of open-source data extraction tools available in the market, only National Institute of Standards and Technology (NIST)-standard tools such as these are admissible in a court of law. Such tools are sold only to state enforcement agencies and we procured them three years ago using Tamil Nadu Innovative Initiative (TANII) funds,” said a senior forensic department official.
A senior scientist from the Chennai lab said data from a cell phone can be extracted using two methods: logical and physical. In the first method, the extraction tool interacts with the phone using its own programming language to retrieve calls and text logs, passwords to social media accounts, saved photos and videos. But it has limitations since deleted and password-protected files can’t be accessed. In the other method, deleted files can be extracted as the tools create a bit-by-bit replica of all the files in the phone, including hidden files in subfolders. Currently, UFED is the most preferred tool by the Chennai lab as it presents the extracted data in a searchable and user-friendly format.
“Despite using such highend tools, extracting and analysing data is becoming increasingly difficult as mobile manufacturers keep updating their products. The type of smartphone, OS and security features determine the amount of access to data. There is no guarantee that all data can be retrieved. But the forensic tool firms also keep updating their products at regular intervals to meet the challenge,” the scientist told TOI.
(*name changed)







