
Some enterprising hackers have already discovered an exploit on the just-launched Nintendo Switch 2. Bluesky user David Buchanan was the first to show off the exploit, where he apparently discovered a weakness in the console’s shared library.
This vulnerability, called a userland Return-Oriented Programming exploit, allows Buchanan to manipulate a program by overwriting its return address to another piece of code. When chained together, this can force the system to work in an unintended manner — in this case, display custom checkerboard graphics.
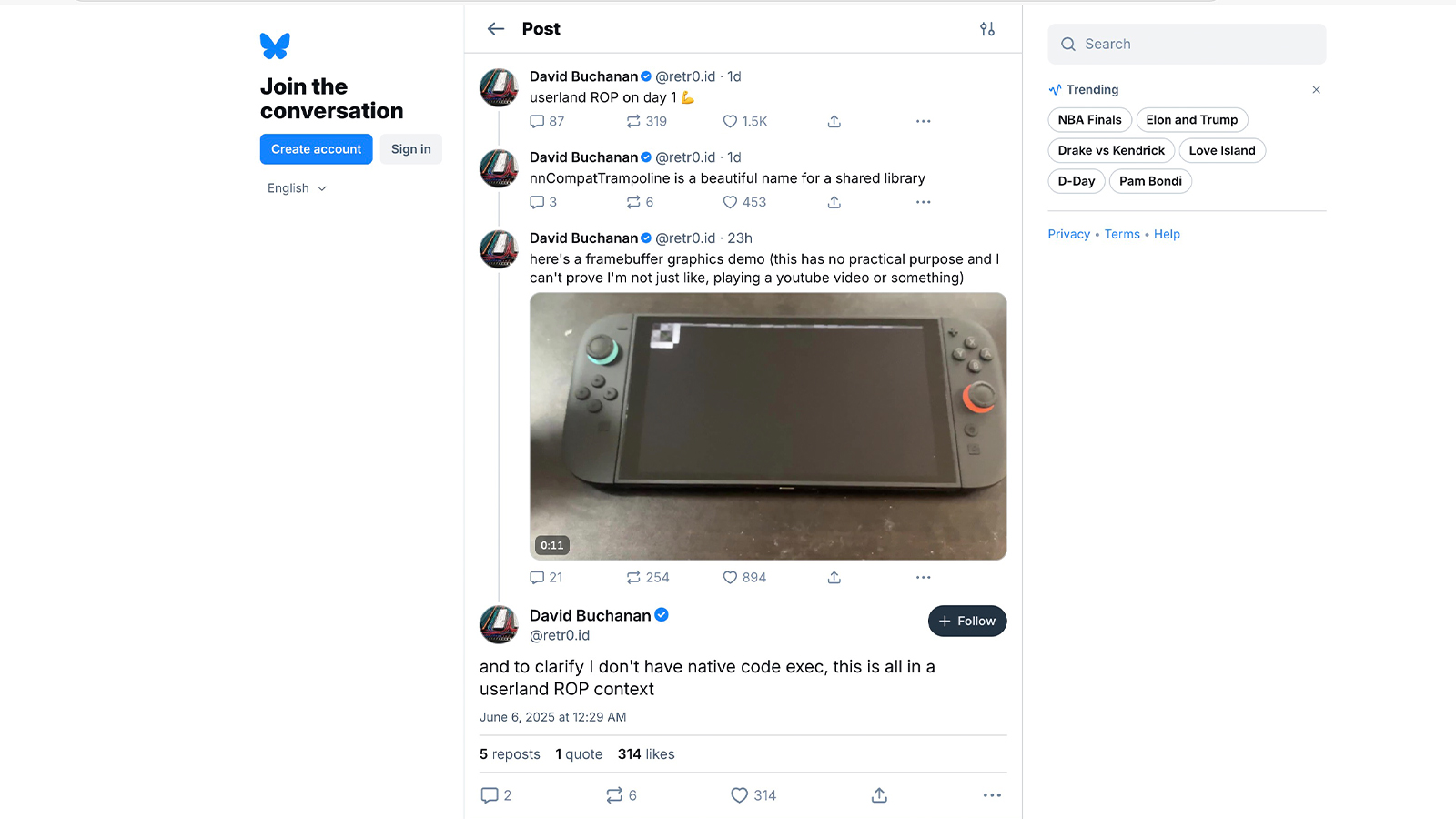
Since this is only a userland exploit, it only runs on the user level and does not affect the Switch 2’s kernel, nor does it give you root access to the device. Buchanan said that this has no practical purpose, meaning this won’t jailbreak the console and allow users to modify it in unintended ways. They even admitted that they can’t prove that they’re running an exploit instead of just playing a YouTube video, although other developers and modders have confirmed that the exploit does exist.
The Japanese gaming giant is known for proactively protecting its intellectual property rights. It has gotten to the point that the company said it may brick your console if you use it to modify Nintendo Account Services, and the Switch 2 user agreement is pretty firm about not modifying software.
Since the Switch 2 has just been released, it will likely take weeks, months, or even years before someone discovers a way to defeat the company’s built-in protections on the handheld. If and when someone finally jailbreaks the Nintendo Switch 2 and creates a custom homebrew OS, we can then see how Nintendo will react.
Follow Tom's Hardware on Google News to get our up-to-date news, analysis, and reviews in your feeds. Make sure to click the Follow button.





.jpg?w=600)

