Looks like hackers are trying to flog a fresh batch of user passwords on the web, again. Or are they? A recent report has been rotating around the web claiming that 16 billion passwords are up for grabs following a "record-breaking data breach", though many cybersecurity experts argue it's not what it seems.
The original report comes from Cybernews, an outlet that previously claimed to have knowledge of a breach of 10 billion passwords last year, and 26 billion records just before that. Woah, that suggests password breaches in excess of billions happen all the time… or do they?
Turns out, what's likely happening here is that someone is putting together one Very Big File including the many data breaches that have occurred in the past. That is, it's not a new data breach; it's a collection of previous ones, known as a package or simply a collection. In this case, this may not even be a single collection: the researcher behind it, Bob Diachenko, says it is from multiple sources, bound together to get to that 16 billion figure. That's the 'breach' that Cybernews is reporting—less of a breach, more of a compilation of breaches from the past however many years. Now That's What I Call Breaches.
Here are well-known malware and cybersecurity experts, vx-underground, on the new package:
No.It's common for Threat Actors to take collections of compromised websites and assemble them into packages. There are many packages available.The thing CyberNews discussed was a new "pack" which contains 16,000,000,000 records. This is true, a new "package" does exist.…June 19, 2025
Here's another account with a similar note:
16 Billion Credentials Leaked – What Actually Happened?Cybernews first broke the story, reporting that their team had discovered multiple smaller datasets over the past six months. When combined, the data amounts to over 16 billion credentials.Many major media outlets have…June 19, 2025
Vx-underground makes another good point: if this many passwords had indeed been breached, why aren't any of the companies affected talking about it? And why didn't they talk about the last breach of 26 billion accounts or the billions before that?
According to some reports, Apple, Google, and Facebook have all been included in this breach, and yet these companies remain notably silent on the matter. Looking across various social media platforms, it seems the only people talking about it are other news outlets and a litany of verified accounts on X pushing conspiracy theories about perceived government backdoors being supposedly to blame.
But is there anyone or anything to blame here, beyond poor cybersecurity practices over the past few decades? This collection likely came about from a gradual process of hacks occurring over a very long period of time through various channels, using a range of attacks, schemes, and tools.
CyberNews pushed the same fucking story last year. It's even written by the same author.You can't keep fear mongering people every time a Threat Actor assembles a data leak package pic.twitter.com/NlcjYyWQ95June 19, 2025
Here's Infostealers on the supposed breach. They claim there's no evidence of a mass infection that could lead to any number of computers being breached to reach this 16 billion figure. They also claim the package is likely filled with recycled or even fabricated data. Essentially, they're saying the same thing as vx-underground.
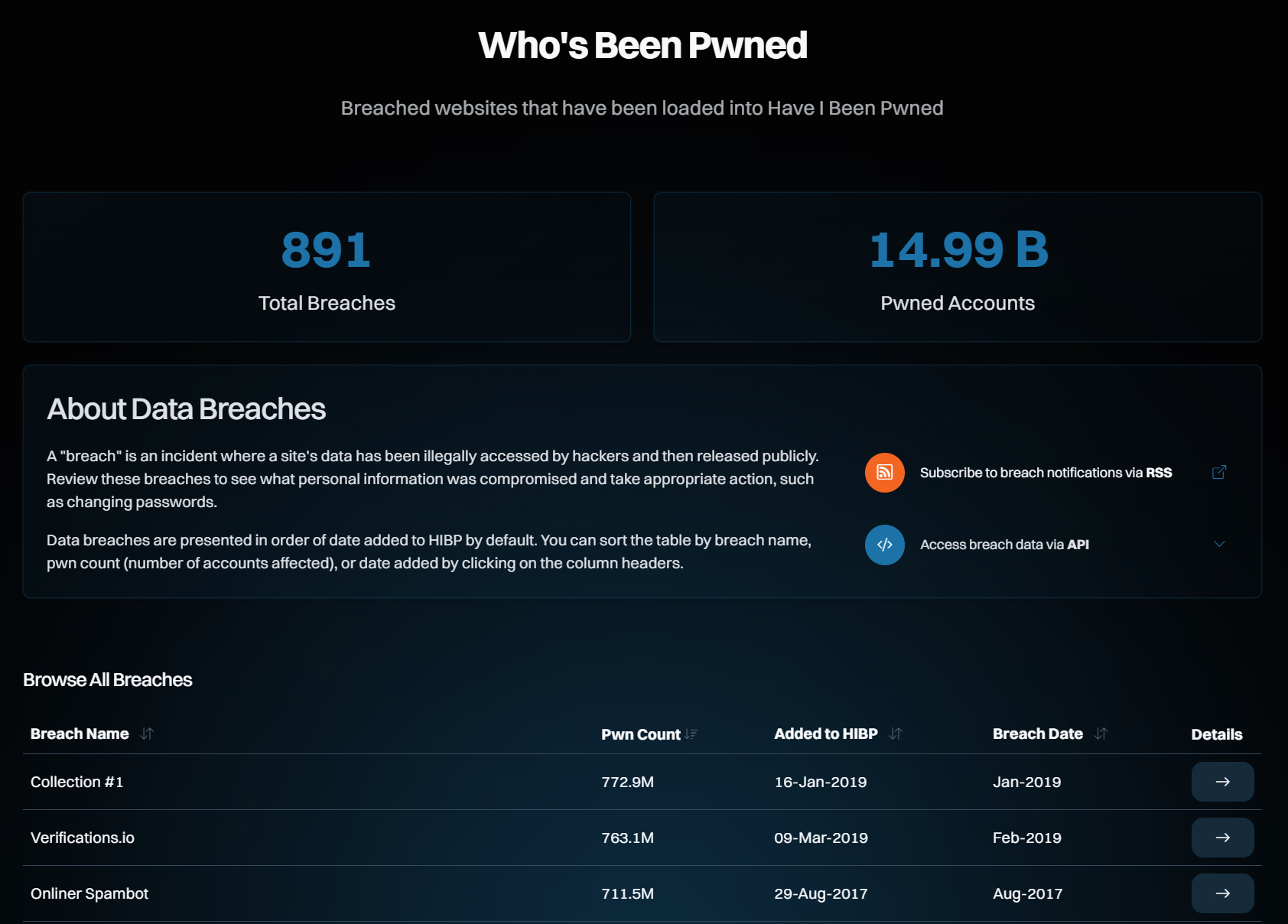
A great way to check your own login details and for any recent breaches is by visiting haveibeenpwned.com. The last breach noted by the site was the Ualabee breach in May 2025, noted in June, containing over 450,000 records from the South American mobility services platform Ualabee. There have been no billions of passwords added to haveibeenpwned's page in recent days.
The largest breach noted by haveibeenpwned is actually a collection of passwords from many sources called Collection #1, which was posted in early 2019. Yep, the same sort of collection as seen here.
So, yes, it's fair to say the language does get a bit fuzzy around what's a data 'breach' and what's not, but a collection of old and likely outdated data poses a significantly reduced risk to a new breach exposing up-to-date information and targeted at a single platform or database. Also note that the 26 billion password breach suggested by Cybernews in 2024 isn't logged in the list.
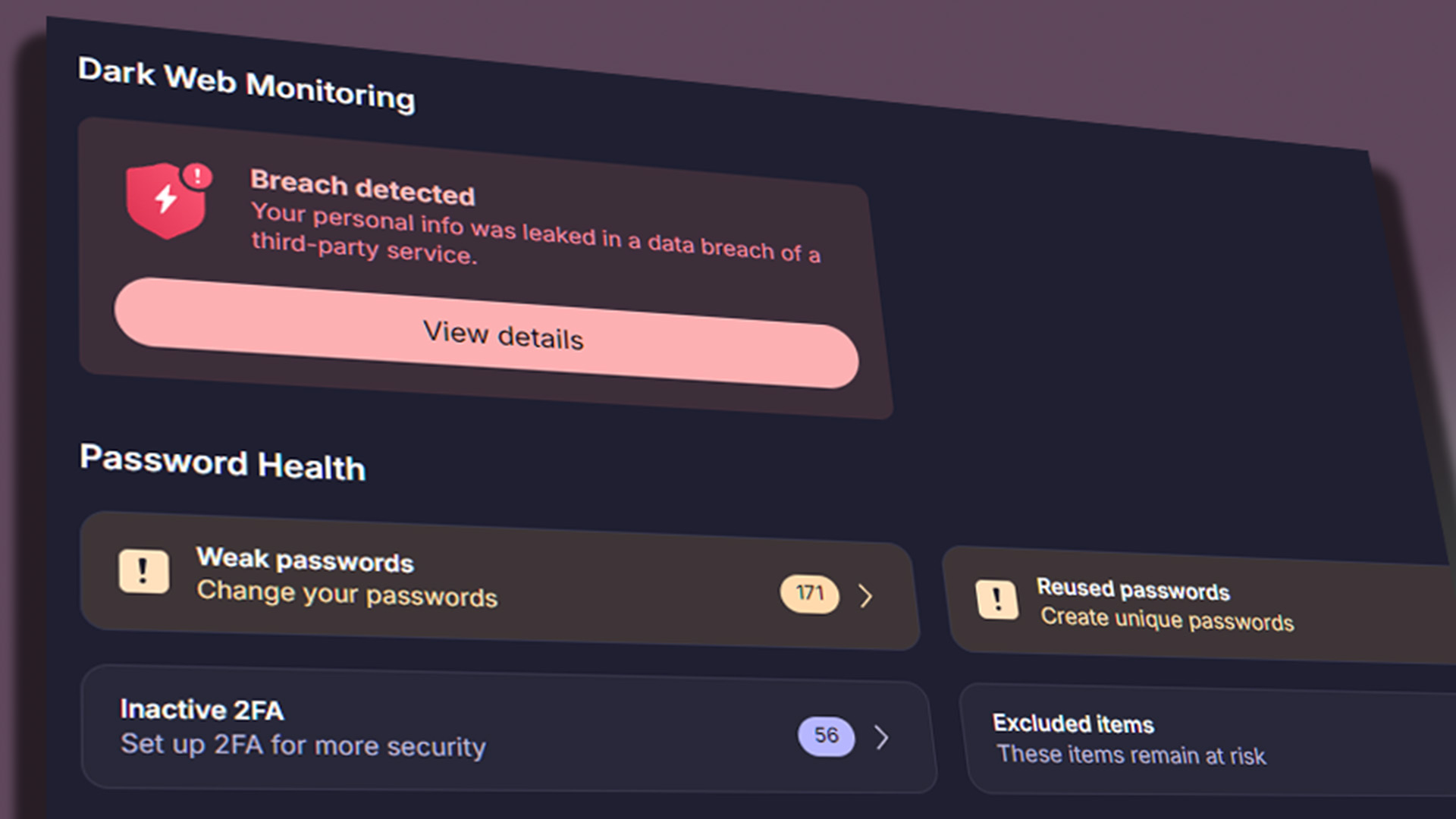
So, should you be worried about your passwords? Well, yes and (a little bit) no. This might not be a new breach of massive proportions as claimed, but it's still a good warning of the dangers of poor cybersecurity practices. If you rely on a single password for multiple websites, you're increasing your risk of theft, fraud, or even identity theft. Grab yourself a password manager—there are many good options, but I'd recommend Bitwarden or Proton Pass from my own experiences with them—and turn on two-factor authentication where possible (2FA).
And don't let me see you use any of the popular passwords noted in NordPass' yearly report, including '123456' and 'password'.
Using a single password for everything was very much my MO when I was a kid, but luckily I lived to see another day, set another password, and with my Runescape account safe. Sadly, I did lose my Adventure Quest login to hackers… don't let those b******s get yours.







