Nomad, a company that provides tools for tokens to be transferred across different blockchains, has suffered from what could be the first ever decentralized robbery in the crypto space. Close to $200 million was drained from the platform by a multitude of users that simply copied the same exploit employed by a single hacker.
Nomad’s hack differs from other crypto exploits, which usually involve a coordinated attack unfolding over a period of time, and instead stems from the work of one rogue actor who was parroted by hundreds of other accounts.
In total, Nomad had $190.7 million stored across its platform, and almost all of the funds were drained in less than a day. Cointelegraph notes that by the time the dust settled, only $651.54 remained in the company’s wallet.
How did it happen? —
Sam Sun, a researcher for a crypto/web3 investment firm, outlined the breach in an informational thread over Twitter, who first noticed something was awry after someone in a Telegram channel called attention to massive amounts of assets leaving the Nomad bridge.
To put it simply, users were able to copy the original hacker’s transaction call data and switch out the address to their own, before sending it through Etherscan, a smart contracts platform. The exploit arose after a Nomad update allowed for part of its code to be verified during transfers. Due to the sheer volume of illicit activity taking place, it can be assumed that some people were creating bots to automate some of the transfers.
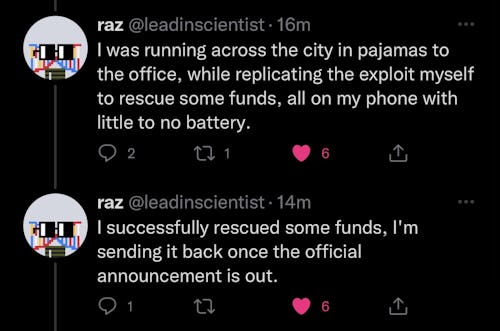
If there’s any bright side here at all, it’s that some white hat users claim to have participated in the hack with the intention of returning the money later on — scooping up funds before bad actors got to them first. It’s not quite ideal proof that crypto’s decentralization has its perks, but it’s better than nothing.
Blockchain bridges have become the de facto target for hackers who expose vulnerabilities in their code. Although the Nomad breach wasn’t highly sophisticated, it illuminates the dangers of faulty, back end programming.







