
Hackers have figured out how to hijack WhatsApp accounts without cracking the messaging app’s encryption, security researchers have warned.
The so-called GhostPairing scam takes advantage of legitimate features in order to trick WhatsApp users into linking their account to a device controlled by an attacker, giving them real-time access to messages, photos, videos and voice notes.
Once in control of an account the hacker can send messages to the victim’s contacts in order to carry out further hijacking attacks.
The exploit works by sending a message to a target, which appears to come from a trusted contact.
A link within the message, which typically claims to show a photo of the the user, takes the victim to a fake Facebook login page that prompts them to enter their phone number.
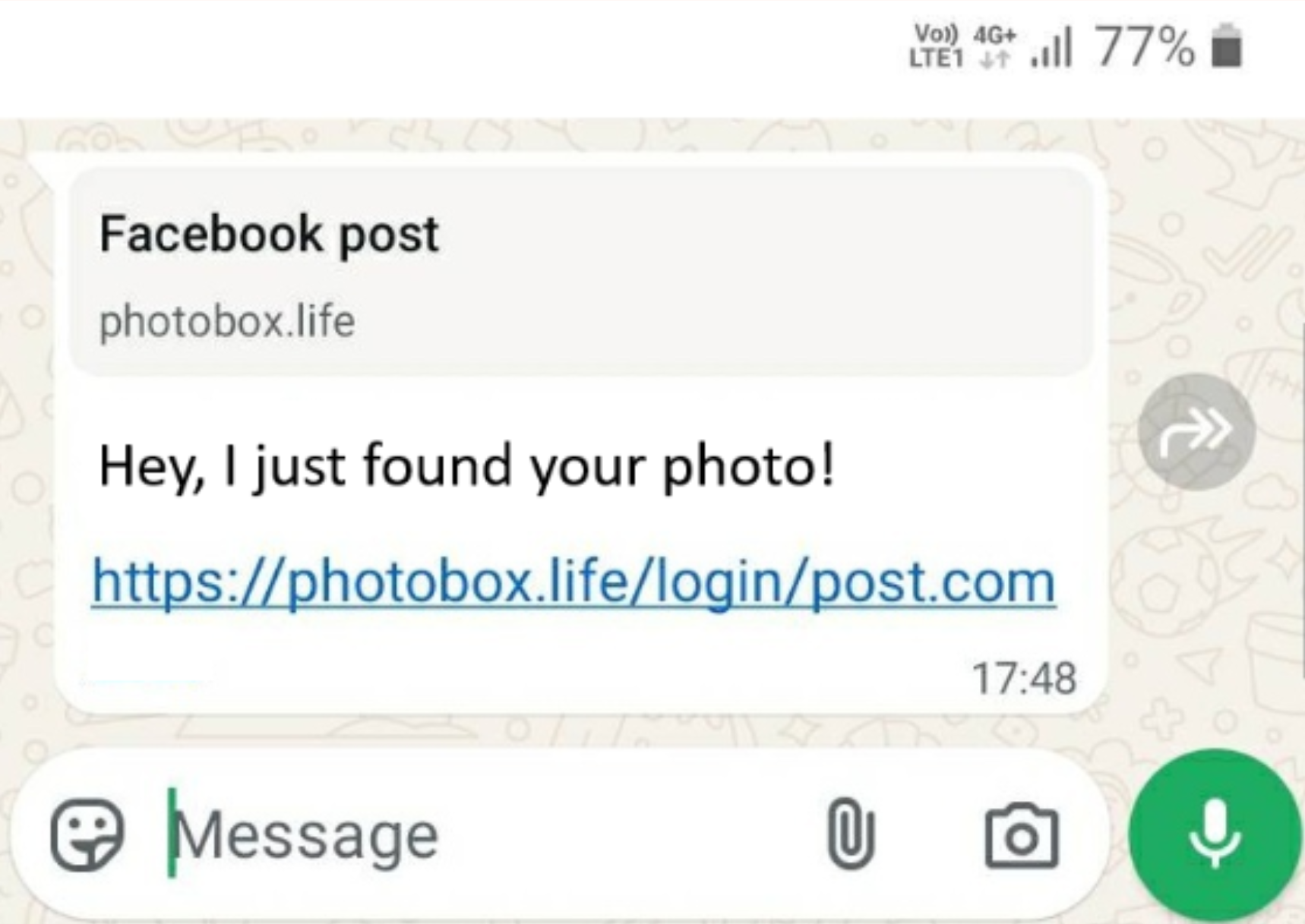
Instead of showing a photo, the page initiates WhatsApp’s device-pairing feature by showing a code that the victim is instructed to enter into the app.
This unwittingly authorises an unknown device to be linked to the account, giving the attacker full access without requiring a password or other authentication credentials.
The scam was uncovered by researchers at the cyber security firm Avast, who warn that the attack is especially concerning because it creates a “snowball effect” that allows it to spread quickly.
“This campaign highlights a growing shift in cybercrime: breaching people's trust is as important as breaching their security systems,” Luis Corrons, a Security Evangelist at Avast, told The Independent.
“Scammers are persuading people to approve access themselves by abusing familiar mechanisms like QR codes, pairing prompts, and ‘verify on your phone’ screens that feel routine.
“Scams like GhostPairing turn trust into a tool for abuse. This isn’t just a WhatsApp issue. It’s a warning sign for any platform that relies on fast, low-visibility device pairing.”
In a blog post detailing the scam, Avast noted that people may have fallen victim to the hijacking attack without even realising it.
WhatsApp users are able to check which devices have access to their account by going to Settings and selecting ‘Linked Devices’. Any devices that are not recognised should be removed immediately.
The Independent has reached out to WhatsApp for comment.
“At Avast, we see this as a turning point in how we think about authentication and user intent,” Mr Corrons said.
“As attacks grow more manipulative, security must account not just for what users are doing intentionally, but also what they’re being tricked into doing. GhostPairing shows that when trust becomes automatic, it becomes exploitable."
Five AI-powered property search apps that could change how you buy your next home
How Google leapfrogged ChatGPT – and why the AI race may already be over
Mystery surrounds a content creator’s livestream appearing on White House website
Starlink satellite is out of control and ‘tumbling’ to Earth
AI data centers created as much pollution as New York City this year, study estimates







